- Introduction
- Step 1: Configure the ports for your SIP Trunk / VoIP Provider
- Step 2: Configure the ports for remote ECLOUD clients
- Step 3: Configuration of ports for Remote IP Phones / Bridges via Direct SIP
- Step 4: Configuration of ports for 3CX WebMeeting
- Step 5: Disable SIP ALG
Introduction
If you plan to use remote extensions or a VoIP Provider, you will have to make changes to your firewall configuration, in order for 3CX Phone System to communicate successfully with your SIP trunks and remote IP Phones. This chapter gives you a generic overview of the ports that need to be opened/statically forwarded on your firewall. We also have detailed guides for popular firewalls that take you step by step to the correct configuration of your firewall. You can learn more about Routers, NAT, VoIP and Firewalls in this article.
Step 1: Configure the ports for your SIP Trunk / VoIP Provider
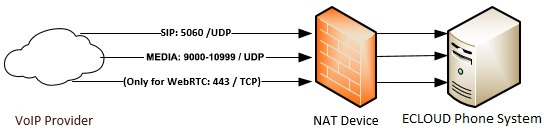
Open the following ports to allow ECLOUD Phone System to communicate with the VoIP Provider/SIP Trunk & WebRTC:
- Port 5060 (inbound, UDP) for SIP communications
- Port 9000-10999(inbound, UDP) for RTP (Audio) communications, which contain the actual call. Each call requires 2 RTP ports, one to control the call and one for the call data. Therefore, you must open twice as many ports if you wish to support simultaneous calls.
Step 2: Configure the ports for remote ECLOUD clients
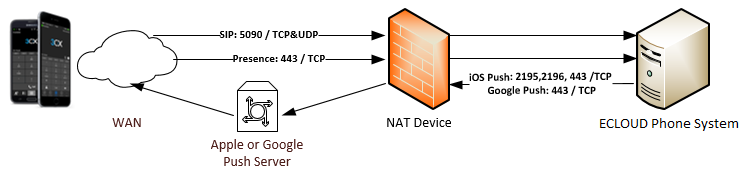
To allow users to use their ECLOUD clients remotely, on Android, iOS, Mac or Windows, you must open the following ports:
- Port 5090 (inbound, UDP and TCP) for the ECOUD tunnel
- Port 443 or 5001(inbound, TCP) HTTPS for Presence and Provisioning
(Unless you have chosen custom ports). - Port 443 (outbound, TCP) for Google Android Push:
- Port 2195, 2196 (outbound, TCP) for Apple iOS Push
Step 3: Configuration of ports for Remote IP Phones / Bridges via Direct SIP
For remote IP Phones and bridges you have the choice of using the ECLOUD SBC (Tunnel) or Direct SIP. The ECLOUD SBC service will bundle all VoIP traffic over a single port and vastly simplify firewall configuration and improve reliability. No additional configuration is required because the ECLOUD SBC will use the same ports as the ECLOUDPhone clients use.
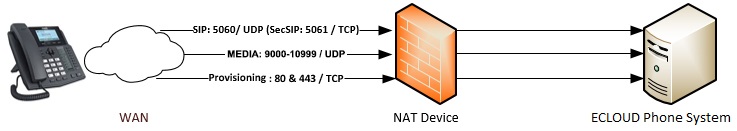
If you wish to connect remote extensions via direct SIP, you must open the following ports (most of them are already opened if you use a SIP trunk):
- Port 5060 (inbound, UDP and TCP), Port 5061 (inbound, TCP) (if using secure SIP) – already open if using SIP Trunks.
- Port 9000-10999 (inbound, UDP) for RTP – already open if using SIP Trunks.
- Port 443 or 5001(inbound, TCP) HTTPs for provisioning. (Unless you have chosen custom ports
Step 4: Configuration of ports for ECLOUD WebMeeting
In order to be able to create and participate in web based meetings the ECLOUD hosted cloud service must be able to communicate with the ECOUD pbx and vice versa. In order to do so the following ports need to be forwarded and outbound traffic needs to be allowed to:
- Port 443 (outbound, TCP) to webmeeting.ECLOUD.net (the ip may changes and it is recommended to allow traffic to the fqdn rather then to the ip address when possible)
- Port 443 or 5001 (inbound, TCP unless you have chosen custom ports) to notify users of incoming web meetings
- Open the port you selected for HTTPS inbound TCP on your firewall inbound TCP. The default is 443 but if you changed it to 5001 or another custom port, open that port.
Step 5: Disable SIP ALG
To maximize your chances of success, make sure you choose a device that does not implement a SIP Helper or SIP ALG (Application Layer Gateway), or choose a device on which SIP ALG can be disabled. The following links are examples of how to switch off ALG on popular routers:
